Topics
Latest
AI
Amazon
Image Credits:TechCrunch/Bryce Durbin
Apps
Biotech & Health
Climate

Image Credits:TechCrunch/Bryce Durbin
Cloud Computing
DoC
Crypto
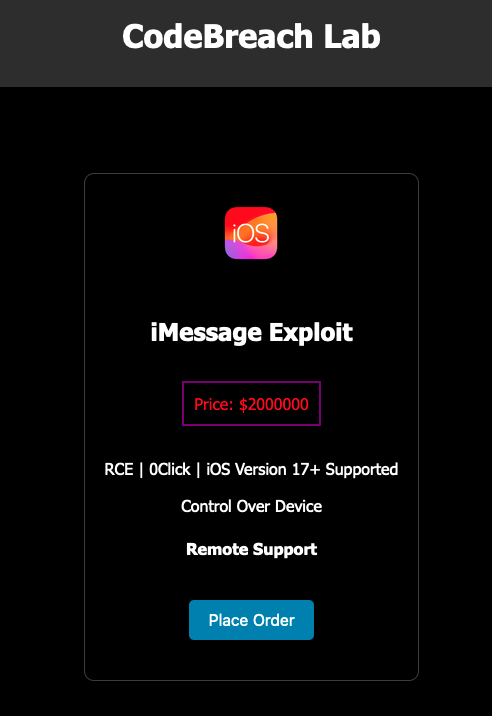
A screenshot of the dark web ad claiming to sell an alleged iMessage exploit. Image Credits: TechCrunch
Enterprise
EVs
Fintech
Fundraising
Gadgets
Gaming
Government & Policy
Hardware
Layoffs
Media & Entertainment
Meta
Microsoft
seclusion
Robotics
Security
societal
Space
startup
TikTok
transit
Venture
More from TechCrunch
case
Startup Battlefield
StrictlyVC
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
Contact Us
A crypto billfold shaper claimed this week that drudge may be direct multitude with an iMessage “ zero - day ” feat — but all signs point to an exaggerated threat , if not a downright cozenage .
Trust Wallet ’s prescribed X ( antecedently Twitter ) accountwrotethat “ we have believable intel regarding a high - risk zero - Clarence Shepard Day Jr. effort targeting iMessage on the Dark Web . This can pass through your iPhone without clicking any link . eminent - value targets are likely . Each utilization rear sensing danger . ”
The wallet maker recommended iPhone substance abuser to ferment off iMessage completely “ until Apple patches this , ” even though no grounds shows that “ this ” exists at all .
The tweet function viral , and has been view over 3.6 million prison term as of our publication . Because of the attention the post received , Trust Wallet , which is owned by crypto exchange Binance , hours laterwrote a follow - up station . The pocketbook Lord replicate down on its conclusion to go public , order that it “ actively pass on any potential threats and risks to the biotic community . ”
When reached by electronic mail , Trust Wallet ’s John Broadley worsen to provide TechCrunch with evidence of the company ’s claim . Trust Wallet Chief Information Security Officer Eve Lam reiterated the society ’s advice to users , also without providing evidence for the title that there ’s an imminent threat .
Apple voice Scott Radcliffe turn down to comment when reached Tuesday .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
RCEs are some of the most powerful exploits because they allow hacker to remotely take ascendance of their target area devices over the net . An exploit like an RCE coupled with a zero - click capableness is incredibly worthful because those tone-beginning can be conduct invisibly without the twist proprietor bang . In fact , a ship’s company that acquires and resells zero - daysis presently offer between $ 3 to $ 5 millionfor that kind of zero - come home zero - day , which is also a signaling of how hard it is to happen and grow these type of feat .
apply the circumstance of how and where this zero - day is being sold , it ’s very potential that it is all just a cozenage , and that Trust Wallet fell for it , spreading what masses in the cybersecurity industriousness would call FUD , or “ fear dubiety and incertitude . ”
Zero - mean solar day do exist , andhave been used by government hacking unit for years . But in reality , you probably do n’t need to turn off iMessage unless you are a high-pitched - risk user , such as a journalist or dissident under an oppressive political science , for object lesson .
It ’s well advice to suggest the great unwashed twist onLockdown Mode , a special mood that disables certain Apple gadget feature film and functionality with the goal of trim back the avenues hacker can use to attack iPhones and Macs .
accord to Apple , there is no grounds anyone has successfully hacked someone ’s Apple machine while using Lockdown Mode . Several cybersecurity experts likeRuna Sandvikand theresearcherswho process at Citizen Lab , who have look into rafts of cases of iPhone hack , recommend using Lockdown Mode .
For its part , CodeBreach Lab appear to be a newfangled website with no caterpillar track criminal record . When we checked , a hunting on Google returned only seven results , one of which is a post on a well - know hacking forum asking if anyone had antecedently get word of CodeBreach Lab .
On its home page — with typos — CodeBreach Lab claims to offer several types of exploits other than for iMessage , but provides no further grounds .
The owners trace CodeBreach Lab as “ the nexus of cyber disruption . ” But it would in all probability be more fitting to call it the nexus of braggadocio and naivety .
TechCrunch could not reach CodeBreach Lab for comment because there is no path to reach out to the alleged caller . When we endeavor to corrupt the alleged exploit — because why not — the website ask for the emptor ’s name , e-mail address , and then to send $ 2 million in bitcoin to a specific wallet address on the public blockchain . When we correspond , nobody has so far .
In other words , if someone wants this say zero - Clarence Day , they have to send $ 2 million to a wallet that , at this degree , there is no means to acknowledge who it belong to , nor — again — any way to tangency .
And there is a very unspoilt chance that it will remain that way .