Topics
Latest
AI
Amazon
Image Credits:Bryce Durbin/TechCrunch
Apps
Biotech & Health
Climate
A screenshot of X’s audio and video calling feature on iOS.Image Credits:TechCrunch
Cloud Computing
Commerce
Crypto
A screenshot of X’s audio and video calling feature on Android.Image Credits:TechCrunch
Enterprise
EVs
Fintech
A screenshot of the settings for X’s audio and video calling feature for iOS.Image Credits:TechCrunch
Fundraising
Gadgets
gage
A screenshot of the settings for X’s audio and video calling feature for Android.Image Credits:TechCrunch
Government & Policy
Hardware
Layoffs
Media & Entertainment
Meta
Microsoft
concealment
Robotics
Security
Social
distance
Startups
TikTok
Transportation
Venture
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
Contact Us
In his pursuit to wrench a simple and officiate Twitter app into X , the everything app that does n’t do anything very well , Elon Musk launch audio and video career on ecstasy last workweek — and this new feature film is switched on by default , it leaks your IP address to anyone you talk with , and it ’s fabulously confusing to figure out how to limit who can call you .
In a post on Wednesday , X ’s official word accountannounced the fresh feature of speech : “ audio and television calling are now uncommitted to everyone on X ! who are you calling first ? ” ten drop a line .
We looked at X ’s official aid heart page and hunt down tests of the feature to canvass how the calling feature whole kit and to sympathise the risks assort with it .
A someone ’s IP address is not enormously tender , but these online identifiers can be used to derive locating and can be linked to a individual ’s on-line natural action , which can be dangerous for high - jeopardy drug user .
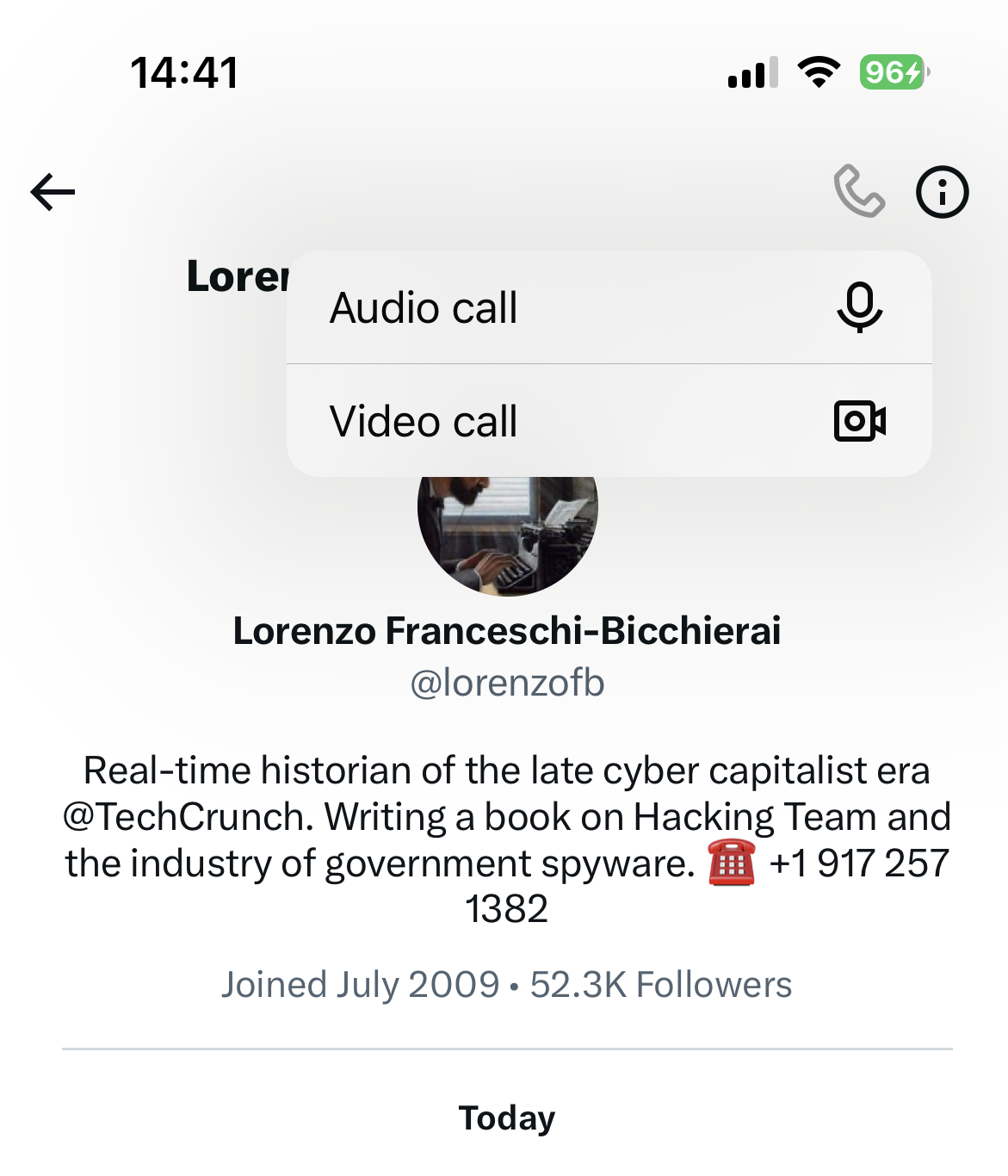
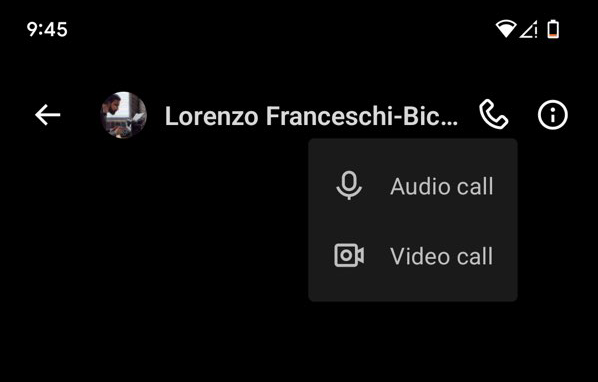
First of all , the audio and video name feature is inside the Messages part of the X app , where a phone picture now appear in the top proper - script corner , both on iOS and Android .
Calling is enabled by nonpayment in the X apps . The caveat is that you’re able to only make and receive call on X ’s app , and not yet in your web browser .
By default option , calls are compeer - to - peer , which entail that the two hoi polloi in a call share each others ’ IP address because the call connects to their devices straight . This materialize by pattern in most electronic messaging and calling apps , such as FaceTime , Facebook Messenger , Telegram , Signal , and WhatsApp , as we reported in November .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
Inits prescribed help essence , X says that call option are root peer - to - peer between exploiter in a way that IP addresses “ may be visible to the other . ”
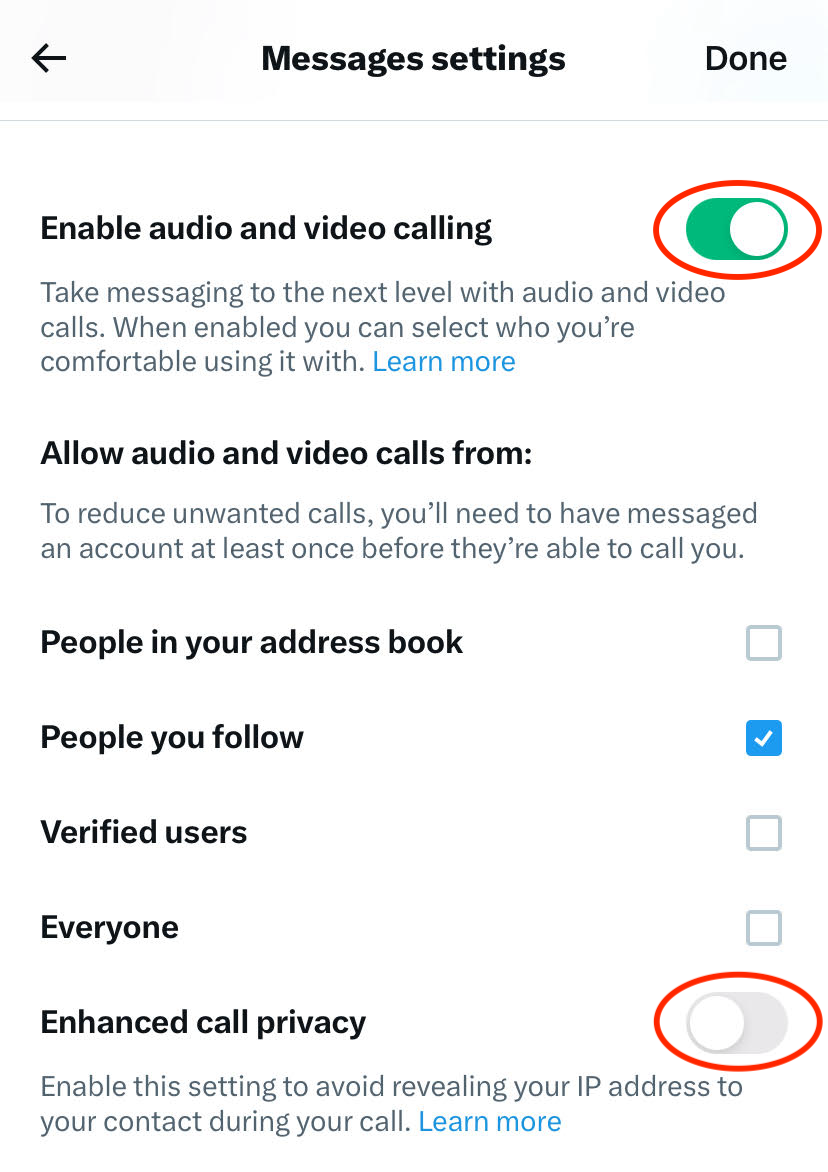
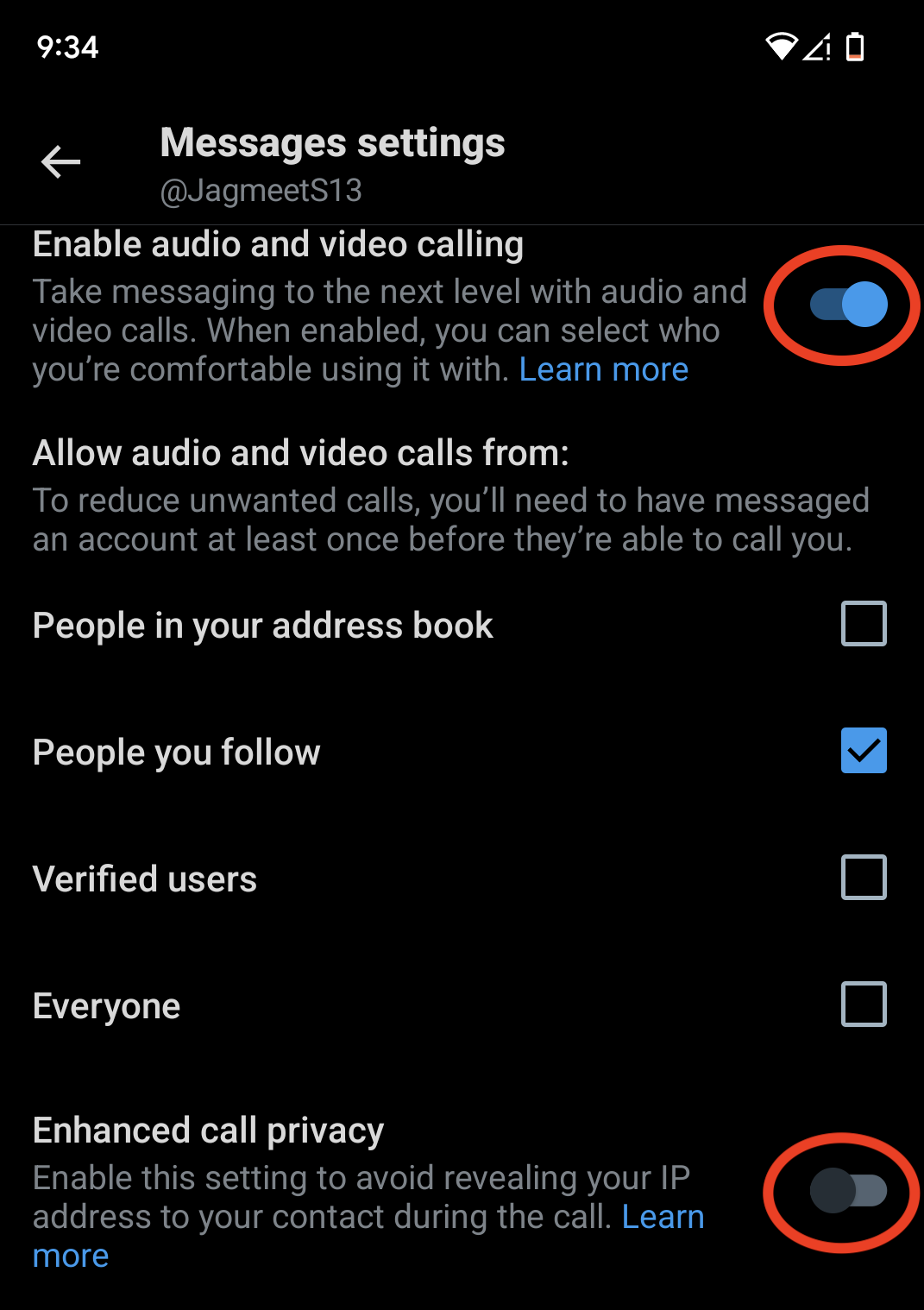
If you want to veil your IP address , you may sprain on the on/off switch “ raise call privacy ” in X ’s Message mount . By flip on this background , X says the call “ will be relay through X base , and the IP destination of any party that has this setting enable will be block out . ”
X does n’t refer encryption in the official aid snapper page at all , so the calls are probably not end - to - final stage encrypt , potentially appropriate Twitter to hear in on conversations . End - to - conclusion encrypted apps , Signal or WhatsApp — prevent anyone other than the company and the recipient from listening in , include WhatsApp and Signal .
We asked X ’s press e-mail whether there is end - to - end encryption . The only reception we got was : “ Busy now , please delay back later , ” X ’s nonremittal motorcar - reception to media inquiries . We also emailed X interpreter Joe Benarroch but did not hear back .
Because of these privacy risk , we commend switch off the calling feature completely .
In case you do need to habituate this call feature , it ’s authoritative to understand who can call you and who you’re able to call — and look on your setting , it can get very puzzling and complicated .
The default scene ( as you may see above ) is “ People you follow , ” but you may choose to alter it to “ People in your address book , ” if you shared your contacts with X ; “ aver users , ” which would allow anyone who pay for X to call you ; or everyone , if you would like to get junk e-mail calls from anyrando .
TechCrunch decide to test several dissimilar scenarios with two decade accounts : a newly produce run account and a long - standing real bill . Using unresolved source internet analysis prick Burp Suite , we could see the web dealings flowing in and out of the X app .
Here are the results ( at the time of composition ):
The connection depth psychology shows that X built the calling feature using Periscope , Twitter ’s livestreaming serving and appthat was discontinued in 2021 . Because X ’s career uses Periscope , our web analysis demonstrate the X app creates the call as if it were a live Twitter / X program , even if the content of the call can not be get word .
Ultimately , whether to use X calling is your choice . you’re able to do nothing , which potentially exposes you to calls from people you probably do n’t need to get calls from and can compromise your privacy . Or you’re able to seek to limit who can call you by decipher X ’s configurations . Or , you may just switch off the feature altogether and not have to worry about any of this .
Carly Page and Jagmeet Singh contribute reporting .
How to keep your Twitter secure without giving Elon Musk any money