Topics
Latest
AI
Amazon
Smashed iPhones are seen during COP28 in Dubai, United Arab Emirates on November 30, 2023.Image Credits:Beata Zawrzel/NurPhoto via Getty Images
Apps
Biotech & Health
Climate

Smashed iPhones are seen during COP28 in Dubai, United Arab Emirates on November 30, 2023.Image Credits:Beata Zawrzel/NurPhoto via Getty Images
Cloud Computing
Department of Commerce
Crypto

An iPhone Security Research Device with stickers and instructions.Image Credits:Gergely Kalman
Enterprise
EVs
Fintech
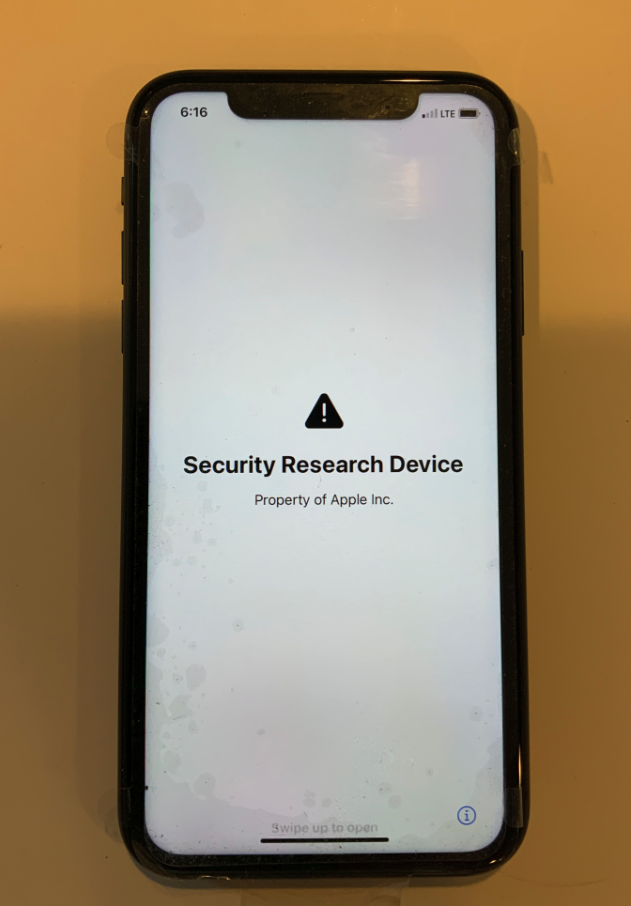
An iPhone Security Research Device.Image Credits:Hoyt LLC
Fundraising
Gadgets
Gaming
Government & Policy
Hardware
layoff
Media & Entertainment
Meta
Microsoft
seclusion
Robotics
protection
Social
blank
inauguration
TikTok
DoT
speculation
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
Podcasts
picture
Partner Content
TechCrunch Brand Studio
Crunchboard
touch Us
In 2019,Apple announced it would start sending some security researchers a “ special ” interlingual rendition of the iPhonedesigned to be used to find vulnerabilities , which could then be reported to Apple so the company could bushel them . In 2020,the ship’s company depart ship the equipment , which are designed to have some security feature disenable , make it easy for researchers to trace bugs in iOS .
Before these gadget exist , there wasa loosely organized mathematical group of hackers and security system researchers who were hell - bended on removing the restrictions Apple put on iPhones , known as the “ jailbreakers . ” The term issue forth from the conception of breaking out of Apple ’s security limitation — dubbed a “ jail ” — on the iPhone .
The jailbreaker ’s goals were sometimes just to have playfulness mother around restrictions , such as sideloading apps not included in the official App Store , and — back in the day — to only exchange the iPhone ’s background before that feature was enabled .
Despite these apparently innocuous end , Apple engage war against the jailbreakers for years , discourage citizenry from disabling the security feature of their iPhones . There is still at least oneApple keep pagethat call jailbreaking “ unauthorized modifications ” to iOS .
As for these days , Apple appears to have embraced the term jailbreaking by using it in the prescribed instructions of the Security Research equipment , according to a photograph post on X ( antecedently Twitter)by security researcher Gergely Kalman .
“ We ’ve made it simple to get your live tooling play on the Security Research machine . Through the cryptex subsystem , you’re able to side load your tooling and it will hunt down with platform privilege and any entitlement you ’d wish , ” the instructions read . “ This allows the rest of the surety insurance policy to continue enabled , provide the tractableness of a jailbroken twist , while maintain the systems you ’re investigate intact in a client - like state . ”
Kalman admit a image of the box seat holding his iPhone Security Research equipment , a varlet of instructions for investigator and three stickers that he said were inside the loge .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
“ Sorry no unbox video , but here is the Apple Security Research gadget with the swag that was included , ” Kalman wrote in the post that he print on Tuesday .
It ’s ill-defined how many of these Security Research Devices really exist in the natural state , and very few pictures of it have been widely distributed online .
Apple voice Scott Radcliffe did not react to a request for gossip when TechCrunch asked how many of these machine Apple has charge out , and whether the program has led to an increase in the number of vulnerability report to the company .
Kalman told TechCrunch that his Security Research equipment is “ identical ” to an iPhone 14 Pro . The only divergence , he impart , is that at the bottom of the locked screen there is the writing “ Security Research gadget ” and an Apple phone number , presumably to report it if it gets lost .
asunder from that , Kalman sound out there ’s a special tag on the box that says “ Do not take away ” and “ Property of Apple Inc. , ” along with a serial number , whichApple billet on its website . Kalman allege there is also a marking on the side of the phone which enunciate : “ Property of Apple . secret and Proprietary . Call +1 877 595 1125 . ”
Before Kalman ’s Wiley Post on Tuesday , it appears thatthere was only one blog postthat demonstrate image of a Security Research equipment , published in 2022 .
The launching of the Security Research equipment platform was at least in part a response tothe proliferation of iPhone epitome — technically called “ dev - fuse ” devices — that hackers and collector were buying and selling in an underground market .
These “ dev - fused ” devices are essentially iPhones that have not gone through the complete yield unconscious process , or were previously used internally at Apple to prove features , and never intend to terminate up in the deal of consumers . As such , these devices have few of the typical security lineament and restriction found on a steady iPhone . This is what made them particularly appealing for certificate researchers : these equipment make it prosperous for hacker to see bug in the iPhone ’s most - defend code .
That ’s why these devices can cost chiliad of dollars , and why Apple has been cracking down on this gray grocery — as well as offering the alternate Security Research Devices .