Topics
Latest
AI
Amazon
Image Credits:Bryce Durbin / TechCrunch
Apps
Biotech & Health
Climate
![]()
Image Credits:Bryce Durbin / TechCrunch
Cloud Computing
Commerce Department
Crypto
The security researcher pulled our precise location data from iSharing’s servers, even though the app was not sharing our location with anybody else.Image Credits:TechCrunch (screenshot)Image Credits:TechCrunch (screenshot)
go-ahead
EVs
Fintech
Fundraising
Gadgets
Gaming
Government & Policy
ironware
layoff
Media & Entertainment
Meta
Microsoft
Privacy
Robotics
Security
Social
blank
startup
TikTok
Transportation
Venture
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
newssheet
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
Contact Us
iSharing, which has 35 million users, fixed the security flaws
Last workweek when a security measure researcher said he could easily obtain the precise location from any one of the million of users of a wide used phone - trailing app , we had to see it for ourselves .
Eric Daigle , a data processor scientific discipline and economics student at the University of British Columbia in Vancouver , witness the vulnerability in the track app iSharing as part of an investigation into the security of location - tracking apps . iSharing is one of the more popular location - tracking apps , claiming more than 35 million users to date .
Daigle said the hemipteran set aside anyone using the app to access anyone else ’s coordinates , even if the drug user was n’t actively deal their location data with anybody else . The bugs also exposed the user ’s name , profile pic and the email address and phone telephone number used to access to the app .
The bugs meant that iSharing ’s servers were not properly checking that app users were only leave to access their placement data or someone else ’s location datum shared with them .
emplacement - trailing apps — includingstealthy“stalkerware”apps — have a history of security mishaps that peril leak or expose user ’ precise placement .
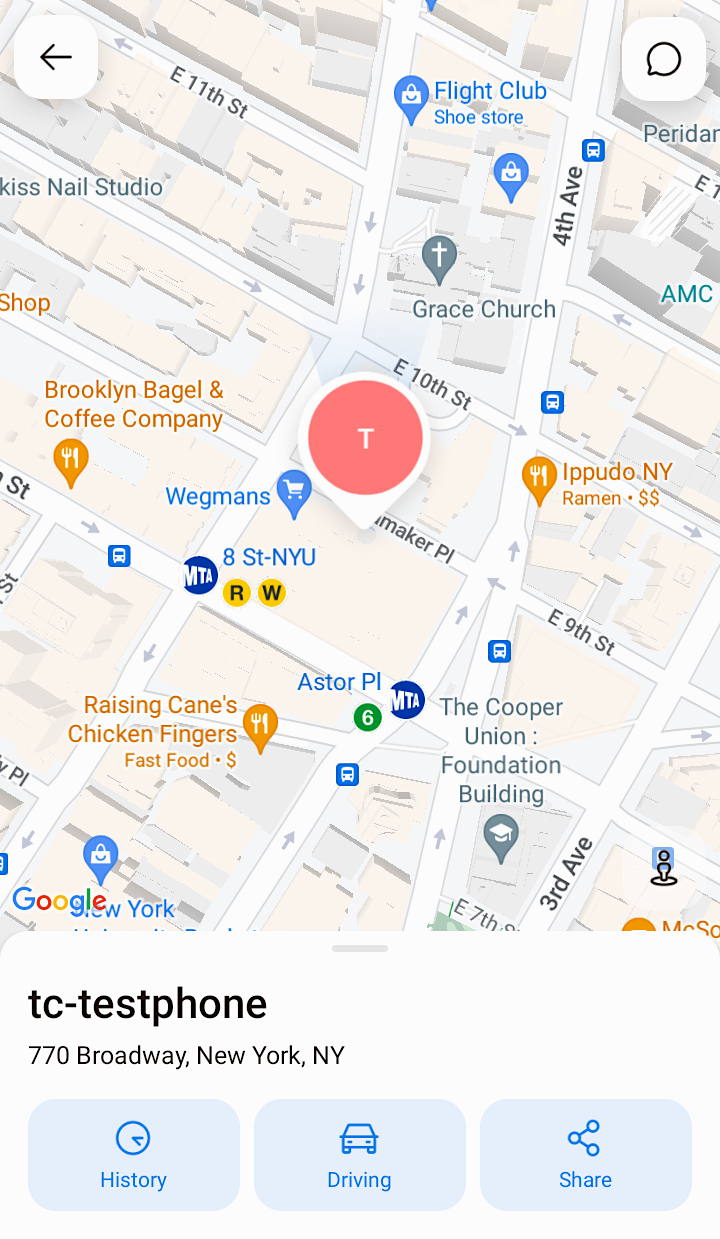
In this case , it took Daigle only a few seconds to turn up this reporter down to a few fundament . Using an Android phone with the iSharing app instal and a novel exploiter chronicle , we necessitate the researcher if he could pull our precise location using the bugs .
“ 770 Broadway in Manhattan ? ” Daigle responded , along with the exact coordinate of TechCrunch ’s bureau in New York from where the phone was pinging out its location .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
Daigle share details of the exposure with iSharing some two weeks originally but had not heard anything back . That ’s when Daigle postulate TechCrunch for assist in contacting the app makers . iSharing fixed the bugs presently after or during the weekend of April 20 - 21 .
“ We are grateful to the research worker for discovering this issue so we could get onwards of it , ” iSharing co - founder Yongjae Chuh told TechCrunch in an email . “ Our squad is presently plan on puzzle out with security professional person to add any necessary security measures to make indisputable every user ’s data point is protected . ”
iSharing fault the exposure on a feature of speech it calls groups , which permit users to apportion their positioning with other user . Chuh assure TechCrunch that the party ’s log render there was no evidence that the germ were find prior to Daigle ’s find . Chuh yield that there “ may have been superintendence on our end , ” because its servers were failing to find out if exploiter were allowed to join a group of other exploiter .
TechCrunch hold the publishing of this tarradiddle until Daigle sustain the fix .
“ rule the initial flaw in aggregate was plausibly an minute or so from opening the app , figuring out the form of the requests , and see that creating a group on another exploiter and joining it work , ” Daigle told TechCrunch .
From there , he spend a few more hour building a proof - of - concept handwriting to exhibit the surety germ .
Daigle , who describe the vulnerabilitiesin more detail on his blog , said he plans to keep enquiry in the stalkerware and emplacement - trailing field .
register more on TechCrunch :
To touch this newsman , get in touching on Signal and WhatsApp at +1 646 - 755 - 8849 , orby email . you’re able to also send file and documents viaSecureDrop .