Topics
Latest
AI
Amazon
Image Credits:Kelvin Chan / AP
Apps
Biotech & Health
mood

Image Credits:Kelvin Chan / AP
Cloud Computing
Department of Commerce
Crypto
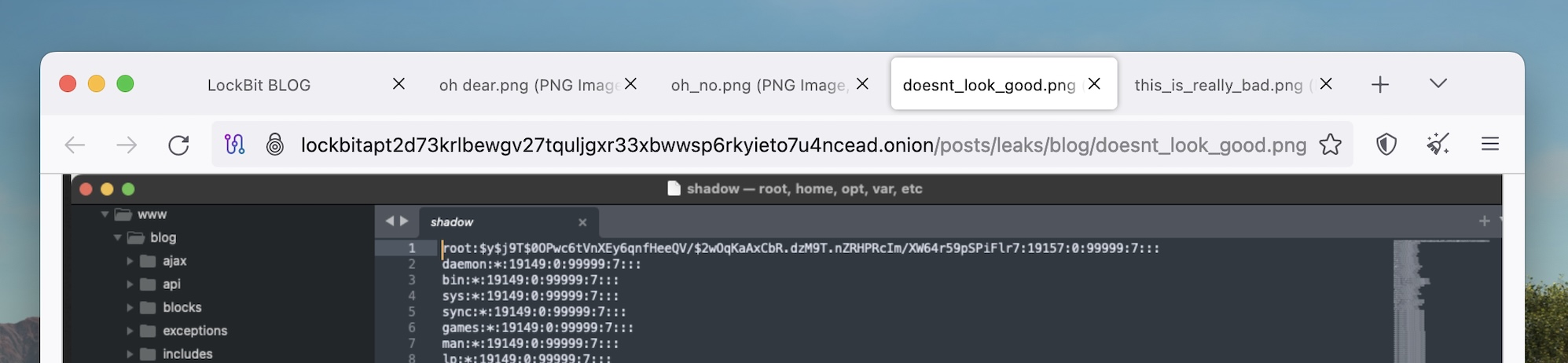
Image Credits:TechCrunch
Enterprise
EVs
Fintech
Fundraising
Gadgets
Gaming
Government & Policy
Hardware
Layoffs
Media & Entertainment
Meta
Microsoft
seclusion
Robotics
security department
Social
blank space
inauguration
TikTok
Transportation
Venture
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
adjoin Us
A wholesale practice of law enforcement military operation led by the U.K. ’s National Crime Agency ( NCA ) this weektook down LockBit , the notorious Russia - linked ransomware pack that for year has play mayhem on commercial enterprise , hospitals , and governments around the world .
The action saw LockBit ’s wetting site downed , its servers seized , multiple hitch made , andU.S. government sanctionsapplied in what is one of the most significant operations taken against a ransomware chemical group to engagement .
It ’s also , undoubtedly , one of the more novel takedown we ’ve seen , with U.K. authorities announce the seizure of LockBit ’s base on the group ’s own leak web site , now home to a host of detail about the crew ’s inner workings — with the hope of more to come .
Here ’s what we ’ve learned so far .
LockBit didn’t delete victims’ data — even if they paid
It ’s long been suspect thatpaying a cyber-terrorist ’s ransom requirement is a gambleand not a guarantee that stolen data will be erase . Some corporate victims have even said as such , tell they“cannot guarantee ” that their data would be erased .
The LockBit squelcher has render us check that this is absolutely the case . The NCA disclose that some of the datum found on LockBit ’s seized system belonged to victims who had pay a ransom money to the threat actors , “ manifest that even when a ransom money is make up , it does not assure that data will be erase , despite what the criminals have promised , ” theNCA tell in a statement .
Even ransomware gangs fail to patch vulnerabilities
Yes , even ransomware gang are slow to piece software bugs . According to malware research groupvx - undergroundciting LockBitSupp , the alleged drawing card of the LockBit operation , law enforcement hack into the ransomware operation ’s servers using a recognise exposure in the democratic web fool language PHP .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
The vulnerability used to compromise its servers istracked as CVE-2023 - 3824 , a outside carrying out flaw patched in August 2023 , hold LockBit months to ready the hemipterous insect .
“ FBI f****d up servers via PHP , backup server without PHP ca n’t be touched , ” reads LockBitSupp ’s read content to vx - underground , originally write in Russian .
Lockbit ransomware grouping administrative faculty has confirmed with us their internet site have been seized.pic.twitter.com/SvpbeslrCd
— vx - underground ( @vxunderground)February 19 , 2024
Ransomware takedowns take a long time
The LockBit takedown , known officially as “ Operation Cronos , ” was eld in the devising , accord to European law enforcement authority Europol . The agencyrevealed Tuesdaythat its investigation into the notorious ransomware ring began in April 2022 , some two years ago at the request of French authorities
Since then , Europol say that its European Cybercrime Center , or EC3 , organized more than two dozen useable coming together and four technical one - week dash to germinate the investigative lead ahead of the net phase of the probe : this week ’s put-down .
LockBit has hacked more than 2,000 organizations
It has long been know that LockBit , which first enter the competitive cybercrime scene in 2019 , is one of , if not the most fertile ransomware gangs .
Tuesday ’s operation all but confirms that , and now the U.S. Justice Department has numbers to back it up . According to the DOJ , LockBit has claim over 2,000 victims in the U.S. and worldwide , and received more than $ 120 million in ransom money requital .
Sanctions targeting a key LockBit member may affect other ransomware
One of the top LockBit membersindictedandsanctionedon Tuesday is a Russian national , Ivan Gennadievich Kondratiev , who U.S. officials allege is involved in other ransomware gang .
concord to the U.S. Treasury , Kondratiev also has ties to REvil , RansomEXX and Avaddon . While RansomEXX and Avaddon are lesser - know variants , REvil was another Russia - based ransomware var. thatgained notoriety for high - profile hacks , pee millions in ransom payments byhacking U.S. connection monitoring giant Kaseya .
Kondratiev was alsonameda leader of a new disclosed LockBit subgroup call in the “ National Hazard Society . ” Little else is known about this LockBit affiliate yet , but the NCA promise to unwrap more in the coming days .
The authority efficaciously ban U.S.-based victims of Kondratiev ’s ransomware from give him the ransom he require . give Kondratiev has hands in at least five unlike ransomware gangs , the indorsement are likely to make his life five clip more difficult .
The British have a sense of humor
Some people ( i.e. , me , a British person ) would argue that we knew this already , but the LockBit sting has prove us that the U.K. authority have a sense of humour .
Not only has the NCA made a mockery of LockBit by mimicking the pack ’s dark web leakage situation for its own LockBit - related Revelation , but we also bump various Easter egg hidden on the now - seized LockBit site . Our darling is the various file names for the site ’s images , which let in “ oh dear.png , ” “ doesnt_look_good.png ” and “ this_is_really_bad.png . ”