Topics
Latest
AI
Amazon
Image Credits:TechCrunch (Screenshot)
Apps
Biotech & Health
clime
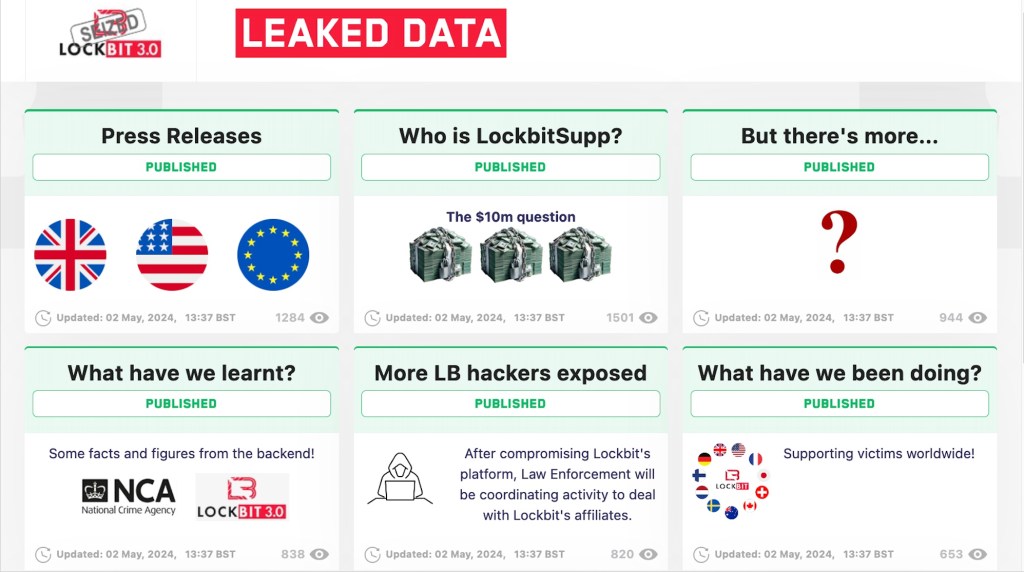
Image Credits:TechCrunch (Screenshot)
Cloud Computing
Commerce
Crypto
Enterprise
EVs
Fintech
Fundraising
Gadgets
gage
Government & Policy
Hardware
layoff
Media & Entertainment
Meta
Microsoft
Privacy
Robotics
Security
Social
infinite
Startups
TikTok
expatriation
Venture
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
Contact Us
On Tuesday , U.S. and U.K. authorities revealed that the mastermind behind LockBit , one of the most prolific and negative ransomware group in story , is a 31 - class - old Russian cite Dmitry Yuryevich Khoroshev , aka “ LockbitSupp . ”
As it ’s customary in these type of announcements , law enforcement published pictures of Khoroshev , as well as detail of his group ’s functioning . The U.S. Department of JusticechargedKhoroshev with several calculator offence , fake , and extortion . And in the procedure , the feds also unveil some point about LockBit ’s past operations .
to begin with this year , authority confiscate LockBit ’s infrastructure and the pack ’s banks of data , revealing key details of how LockBit worked .
Today , we have more detail of what the feds shout out “ a massive criminal organization that has , at time , ranked as the most prolific and destructive ransomware radical in the world . ”
Here ’s what we ’ve learned fromthe Khoroshev indictment .
Khoroshev had a second nickname: putinkrab
LockBit ’s leader was publically have it away by the not - very - imaginative sobriquet LockBitSupp . But Khoroshev also had another on-line indistinguishability : putinkrab . The bill of indictment does n’t include any selective information about the online handle , though it appears to reference Russian President Vladimir Putin . On the internet , however , several profiles using the same moniker onFlickr , YouTube , andReddit , though it ’s undecipherable if these bill were go by Khoroshev .
LockBit hit victims in Russia, too
In the globe of Russian cybercrime , according to experts , there ’s a hallowed , spontaneous convention : hack anyone outside of Russia , and the local authorities will leave you alone . Surprisingly , according to the feds , Khoroshev and his co - conspirators “ also deployed LockBit against multiple Russian dupe . ”
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
It persist to be seen if this mean Russian authority will go after Khoroshev , but at least now they screw who he is .
A leader of what was once the humans ’s most harmful cyber criminal offence grouping has been unmasked and sanctioned by the UK , US and Australia , following an NCA - led international to-do campaign.#Cronos@FBI@EuropolFull story ➡ ️https://t.co / ECxlgOTH5Epic.twitter.com / iYz4w2jheK
Khoroshev kept a close eye on his affiliates
Ransomware operations like LockBit are known as ransomware - as - a - service . That means there are developer who create the software and the infrastructure , like Khoroshev , and then there are affiliate who work and deploy the software , infecting victim , and extorting ransoms . Affiliates pay Khoroshev around 20 % of their legal proceeding , the feds claimed .
agree to the bill of indictment , this occupation simulation allowed Khoroshev to “ closely ” monitor his affiliate , including having access to victim negotiations and sometimes participating in them . Khoroshev even “ demand recognition documents from his affiliate Coconspirators , which he also maintain on his infrastructure . ” That ’s belike how law enforcement was able to identify some of Lockbit ’s affiliates .
Khoroshev also evolve a putz call “ StealBit ” that complemented the main ransomware . This puppet allow affiliates to store data stolen from victims on Khoroshev ’s servers , and sometimes issue it on LockBit ’s official dark web outflow site .
LockBit’s ransomware payments amounted to around $500 million
LockBit launched in 2020 , and since then its affiliates have successfully wring at least just about $ 500 million from around 2,500 victims , which included “ major multinational corporations to lowly businesses and individuals , and they included hospital , school day , non-profit-making organizations , vital infrastructure facilities , and government and law of nature - enforcement agencies . ”
asunder from the ransom payments , LockBit “ caused damage around the universe totaling billions in U.S. dollars , ” because the gang disrupted victim ’ operations and forced many to pay incident reply and recovery services , the feds claimed .
Khoroshev got in touch with the authorities to identify some of his affiliates
belike the most scandalous of the a la mode revelations : In February , after the coalition of global law enforcement agencies get down LockBit ’s website and infrastructure , Khoroshev “ communicated with law enforcement and offered his services in exchange for data regarding the identity of his [ ransomware - as - a - table service ] contender . ”
According to the indictment , Khoroshev asked law enforcement to “ [ g]ive me the name of my enemy . ”